Hello again!
I thought I would do another multi-part post - this time we will use SysInternals ProcMon (v 2.96) monitoring software to investigate the CCleaner (v 3.14.1616) Windows Cleaner program. As this program gets mentioned quite often on the LifeHacker website, I thought I'd try it out. It cleans Temporary (Internet and Windows) files, Browser History (downloads and forms), Cookies, Recycle Bin, the Recent Documents list, old log files and old/unused Registry entries. Since testing completed, an update has been released (3.14.1643).
Once we have finished our (very) basic analysis, we shall then write a RegRipper plugin (in Perl) and test it using the SIFT v2.12 VM. Hopefully, the CCleaner installer will leave some artifacts in the registry which we can then parse using our RegRipper plugin to prove that CCleaner was installed on the PC/see what user settings were set.
You can get your mits on the ProcMon executable here.
The CCleaner installer can be found here.
About CCleaner
 |
| CCleaner "Cleaner" Menu |
 |
| CCleaner "Registry" Menu |
After installing (for all users) and launching, there are 4 main menu buttons on the left hand side of the app window:
- Cleaner (for selecting which Windows/Application log files to clean),
- Registry (for selecting the Registry cleaning settings),
- Tools (running Uninstallers, selecting Windows Startup programs, selecting Internet Explorer startup plugins, removing System Restore Points, setting the (free/whole drive) Drive Wiper settings) and
- Options (Secure Delete and Wipe Free Space settings, Cookies to delete/keep, Folders to delete/exclude, some further Advanced Settings).
As the objective is to write a RegRipper plugin to detect CCleaner installation/settings, we won't be trying to recover any deleted files at this time. Nor will we be investigating the Registry clean of old/unused entries functionality.
Just FYI - there is a "Secure Delete" overwrite setting (under Option-Settings) which can be used to overwrite deleted files from 1 to 35 times. This is not enabled by default but if it works as advertised, I suspect file recovery will be close to impossible.
There is also another option to "Wipe MFT Free Space" but presumably the user must either call the inbuilt "Drive Wiper" tool explicitly OR check the "Wipe Free Space" Cleaner option (not checked by default). A warning does pop up when the check box is selected recommending it stay unchecked for normal use due to the extra time it takes.
Further unchecked by default "Cleaner" Options include:
- Autocomplete Form History
- Saved Passwords
- Network Passwords
- DNS cache
- Old Prefetch data (timeframe unclear)
- tray notifications Cache
- Window Size/Location cache
- User Assist History
Additionally, under Option-Advanced settings, the "Only delete files in Windows Temp folder older than 24 hours" option is checked by default.
As you can see, there's a shedload of CCleaner functionality to investigate. Any takers?
Using ProcMon to analyse CCleaner's Cleaner Function
After launching the ProcMon.exe (does not require installation), the user is first shown a popup filter window. For now, we can "Cancel" it.
In the remaining main window, the capture button (third button from the left) should have a magnifying glass with a red line through it meaning ProcMon is not currently capturing any events. If it doesn't have the red line, toggle the button to stop monitoring.
Now we press the ProcMon capture button and launch the CCleaner program. In the lower part of the Cleaner option window, we press the "Analyze" button and when the analysis completes, we then press the "Run Cleaner" button.
We then exit the CCleaner program and toggle off the capture button in ProcMon.
In ProcMon's File menu, we can save the capture for later review. I chose to save "All Events" in the native PML format.
If you now look at what you've captured (or open the .PML logfile), you can filter out everything except CCleaner events by going to the Filter...filter sub menu (or the Filter pop up window) and then set the drop boxes to read "Process Name" "is" "CCleaner.exe" (probably have to type process name directly) then "Include". Now hit the "Add" button and then the "Apply" and "OK" buttons. The Filter Window generally looks something like this:
 |
| ProcMon Filter Window |
In my capture file, I still had ~200 000 events - clearly, more filtering is necessary.
However, in a rush of excitement / not-so youthful exuberance I started wading into this event list anyway to try to figure out what CCleaner actually does. Here's a brief (and probably incomplete) overview:
- Opens/Reads the CCleaner.exe prefetch file
- Reads the C:\, C:\Documents and Settings, C:\Program Files, C:\Windows directories
- Opens/Reads HKCU\Software\Piriform\CCleaner registry key
- mostly opens/queries but also sets HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2 subkeys
- tries to open various browsers profiles.ini files (presumably so it can find their cache/history files)
- searches thru HKCU\Software looking for applications to clean
- reads C:\RECYCLER
- reads the following directories looking for log (and .dmp) files :
C:\WINDOWS\Temp, C:\Documents and Settings, C:\WINDOWS\Minidump, C:\WINDOWS\system32\wbem\Logs, C:\Documents and Settings\All Users\Application Data\Microsoft\Dr Watson, C:\WINDOWS\Debug,C:\WINDOWS\security\logs, C:\WINDOWS\Logs, C:\WINDOWS\Microsoft.NET
- queries C:\WINDOWS\Prefetch directory
- queries browser profile directories
- calls WriteFile on C:\RECYCLER, C:\Documents and Settings\USERNAME\Recent\*.lnk files, index.dat files, Desktop.ini files, *.log files and (in this case) the Firefox Profiles directory.
Thats kinda where I finished up / lost the will to keep going ...
Getting back to our capture file, we shall try to limit the filter to Registry events only.
Setup/Add/Apply another filter for "Operation" is "RegQueryValue" then "include".
I just chose "RegQuery" value because it sounds like what CCleaner might use to read a CCleaner setting from the registry. There are actually loads more function names to choose from - see the MSDN documentation for registry function calls and for file system function calls.
Anyhow ... you should now see about 1500 events from keys such as HKLM and HKCU.
Scrolling down reveals ... events for the HKCU\Software\Piriform\CCleaner subkey and the HKLM\SOFTWARE\Piriform\CCleaner subkey.
Aha! If CCleaner saves its configuration info to the Registry, we can now create a RegRipper plugin to look for those registry values.
To better view these registry values, we can disable the previous filter and setup another filter - "Path contains Piriform" (also see ProcMon Filter Window pic above). The results indicate that the HKCU subkey contains our CCleaner configuration settings (eg WINDOW_WIDTH, WipeFreeSpaceDrives).
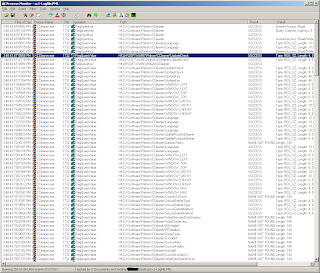 |
| "Path contains Piriform" Filtered Results |
So now we can see that if we create a RegRipper plugin to look for a Software\Piriform\CCleaner subkey and then parse all the values, we can determine what the User's settings were. Stay tuned viewers ... we'll do this in the next exciting installment.
